Think of every endpoint in your corporate network as an invisible employee.
These silent workers never clock in or take breaks, yet they are always active. They power business applications, handle confidential data, and keep operations moving across offices and remote teams.
It’s no wonder IT leaders constantly ask: What is an endpoint, and how can we manage them securely?
The problem is, unlike real employees, endpoints don’t raise their hands when something goes wrong. They can be compromised without warning and turn into open doors for hackers.
Cybercriminals know this and exploit it with phishing, malware, and ransomware attacks that spread fast and put critical information at risk. A single unpatched device can expose your entire corporate network.
For CIOs, the challenge is clear: to unlock the productivity potential of endpoints while keeping them secure. That requires knowing exactly what an endpoint is, how it works, and how it can be an advanced tool that empowers remote workforces to operate at their full capability.
In this guide, we’ll explore the following key questions to make this IT issue clear, including:
- What is an endpoint?
- What is endpoint management in IT?
- How to use endpoint management to scale your digital workplace
Secure your business’s endpoints with FlexxClient. Book a demo to find out how we can keep your organisation’s workforce safe and productive.
What is an endpoint in IT?
In cybersecurity terms, an endpoint is any device that connects to a network and communicates with other systems.
This includes familiar tools like desktop computers, laptops, and mobile devices, but it also extends to servers, Internet of Things (IoT) sensors, smart printers, and even virtual desktops. If it interacts with the corporate network, it qualifies as an endpoint.
Endpoints matter because they are where people, processes, and data intersect. Employees use them to access confidential data, business applications, and cloud services. IT teams rely on them to enforce security policies and manage updates across the organisation.
Yet these same devices can also become the first entry point for cyberattacks. Something as simple as a phishing email opened on a smartphone running outdated software can expose the corporate network to major risks.
It’s also important to distinguish between a REST/API endpoint and an endpoint in IT. Put simply, an endpoint in IT is a physical or virtual device that connects to a network, while an API endpoint is a digital address where software systems send and receive data.
- Q. What is an endpoint in IT?
- A. An IT endpoint is a physical or virtual device that connects to a network.
- Q. What is an endpoint API?
- A. An API (or REST) endpoint is a digital address where software systems send and receive data.
The first type of endpoint, and how to manage it, is what we will focus on for the rest of this article.
What is endpoint management in IT?
One medium-sized organisation can easily have thousands of endpoint devices scattered across its workforce – something that can be a huge headache with remote teams.
Endpoint management helps IT leaders bring all of these under one system of visibility and control, instead of treating each laptop, smartphone or desktop PC as an isolated piece of technology.
The goal is simple: make sure every endpoint is updated, compliant with security policies, and performing optimally without creating extra work for IT teams.
In practice, this means:
- Deploying software updates and patches automatically
- Enforcing rules for accessing confidential data
- Monitoring activity in real time
- Protecting devices even when they’re outside the corporate firewall.
Automation and AI are playing an increasingly important role in the management of endpoints. They make it possible to detect risks faster, reduce manual workloads, and keep endpoints secure without slowing down employees, thus improving the digital employee experience (DEX).
“AI's ability to analyse vast amounts of data quickly and accurately allows organisations to identify and prioritise the most critical vulnerabilities,” says Tony Bradley, founder of TechSpective, an online technology publication. “This is crucial because not all vulnerabilities pose the same level of risk. AI can help determine which vulnerabilities are most likely to be exploited based on the specific context of an organisation's IT environment.”

For CIOs and IT leaders, this modern endpoint management is the framework that helps them scale digital workplaces. It supports business continuity as hybrid and remote workforces grow and turns what could be thousands of unmanaged devices into a cohesive, secure digital ecosystem.
How to use endpoint management to scale your digital workplace
Scaling a digital workplace means more than deploying new tools: it requires managing the endpoints that connect people, data, and applications.
Laptops, smartphones, and PCs drive productivity but also open doors to cyberthreats. This risk is growing at a quickening pace, which is why we’re seeing an explosive rise in the endpoint management market, according market research experts DMR. Their recent report predicts a fivefold increase over the next decade.
The Rise of the Global Endpoint Management Market (2025-2034)
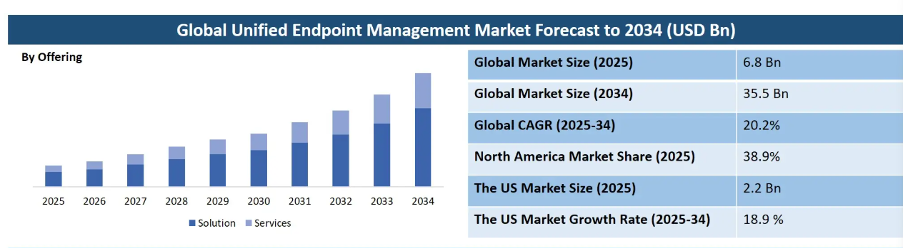
Here’s a look at how managing endpoints in these areas can greatly boost your organisation’s performance.
1. Addressing operational challenges
Efficient endpoint management can help IT teams deal with the day-to-day hurdles IT teams face when managing complex, distributed environments.
Visibility blind spots
Remote devices often operate outside the corporate network. This makes it difficult for IT teams to monitor installed apps, compliance status, or unauthorised access. Fileless malware that hides in memory only increases the risk.
Management complexity at scale
The endpoint landscape is highly fragmented. It is difficult to integrate multiple operating systems, BYOD policies, shadow IT, and IoT devices and failure to do so can leave critical gaps.
The human factor
Human error drives 68% of breaches, whether through phishing clicks or misconfigurations. On top of that, IT teams struggle with alert fatigue and a global cybersecurity talent shortage. Smarter, automated endpoint solutions can keep these errors to a minimum
2. Endpoint security
For IT leaders, the first stop in endpoint management is securing them.
Endpoint security focuses on defending devices and API endpoints against cyberattacks. Since endpoints are often the first places that hackers try to exploit, protecting them requires more than traditional antivirus software. Today’s cyberthreats (malware, ransomware, phishing, and data breaches) demand layered security solutions.
Such measures typically include the following:
Firewalls
Firewalls act as the first line of defence by controlling traffic between internal devices and external networks. They block unauthorised attempts to access endpoints while allowing legitimate communication.
For distributed workplaces, next-generation firewalls also closely inspect traffic and suspicious activities that might otherwise slip through.
Encryption
Confidential data moves constantly across endpoints, whether it’s an employee logging into cloud applications or a mobile device connecting over public Wi-Fi.
Encryption means that even if data is intercepted, it remains unreadable to attackers. Full-disk encryption for laptops and encrypted channels for communication are now baseline requirements for security-conscious enterprises.
Endpoint Detection and Response (EDR)
EDR tools go beyond antivirus by continuously monitoring endpoints for suspicious behaviour.
Instead of relying on known malware signatures, EDR detects unusual patterns, like a sudden surge in file access or an unauthorised process running in the background. IT teams can then respond quickly before threats escalate.
Extended Detection and Response (XDR)
XDR takes security a step further by connecting data from endpoints, cloud applications, email, and network traffic.
This collection of insights from across the IT environment provides a complete picture of potential threats. For CIOs, this unified visibility means faster detection, more accurate alerts, and fewer blind spots.
3. Increase productivity
Endpoints aren’t just risks to be contained; they are powerful enablers of modern business. Each one is a direct channel where employees interact with applications and collaborate across teams and time zones.
Endpoints can accelerate digital transformation when properly managed. They allow IT teams to roll out new software company-wide in minutes and monitor performance trends across the organisation. With these data insights, they can help identify bottlenecks that disrupt productivity.
To make endpoint management really work for your business, consider these best practices:
- Automate updates and patches to close vulnerabilities quickly without disrupting workflows.
- Standardise security policies across all connected devices, ensuring consistent endpoint protection from the office to remote environments.
- Monitor activity in real time to detect unusual behaviour, such as unauthorised logins or suspicious downloads.
- Integrate artificial intelligence and machine learning applications to analyse patterns and predict (and adapt to) emerging threats.
- Use centralised platforms that simplify workplace management across diverse endpoint devices and locations with the help of automation and AI-driven features.
In this way, endpoints evolve into strategic touchpoints that help drive agility and enable new ways of working, keeping your confidential information protected along the way.
By treating endpoints as both strategic assets and security priorities, IT leaders can transform these invisible workers into a foundation for growth, resilience, and a truly agile digital workplace.
Flexxible goes beyond traditional tools to connect and manage all your endpoints, delivering secure, seamless technology experiences that keep your business running and drive measurable outcomes. Book a demo today to strengthen and future-proof your workforce.
Ready to transform your desktop infrastructure? Discover how FlexxDesktop can help your organisation achieve secure, flexible virtual desktops with European data sovereignty.
Recommended for you
- Unlock Hidden Microsoft 365 Savings: The Report IT Leaders Need
- The End of Windows 10 is Near: Are Your Endpoints Ready?
- Tired of Endpoint Chaos? Learn How to Regain Control
- The Best DEX Platforms to Improve Productivity, Security, and Engagement
- The DEX Success Code: Achieving Success with a Service-First Approach
- NIS2 Directive in Spain: Everything You Need to Know to Comply with the Regulation
- Guide to Managing Business Continuity (with examples and tools)
- The Role Of Fairness Measures In AI Product Development: What You Need To Know
- IT Infrastructure: 5 Strategies to Improve Its Productivity
- Automated Scripts: 8 Practical Examples to Optimize IT in Companies


